Table of contents
🥸Introduction to Computer Security Concepts
Computer security refers to measures and controls that ensure the confidentiality, integrity, and availability of the information processed and stored by the computer.
This includes everything from protecting physical information assets to data security and computer safety practices.
Computer security ensures that a business's data and computer system are safe from breaches and unauthorized access.
😎Types of Computer Security
Application security is the process of adding specific features to software that prevent a variety of cyber threats.
e.g., Include 2-step authentication, high-level encryption, logging, firewalls, and many more
Information Security: This revolves around protecting company data assets from unauthorized use.
Network Security: Focuses on the production network administrators implement to avoid unauthorized access, modification, exploitation, or denial of the networks and their resources.
Endpoint security is the practice of safeguarding individual network endpoints—individual devices that connect to an organization's network.
🔴Why is computer security important?
Terminologies
Data theft involves accessing secured, private data assets for the purpose of stealing the data itself or gaining ongoing access to databases for the purpose of corporate espionage.
DOS attacks (Denial of service): They aim to shut down a machine or network with a flood of traffic to make service unavailable for targeted users
DDOS (Distributed Denial of Service): Multiple systems orchestrate an attack on a single target.
Malware is short for malicious software, designed to disrupt a computer system in order to gain access to, take control over, steal, or damage digital assets.
includes computer viruses, worms, trojan horses, ransomware, and many other malware programs.
Backdoors are unintentional vulnerabilities that can give bad actors access to a system without going through normal security procedures.
⚠️Security Attacks
Action that compromises the security of an individual or an organization.
Types of security attacks
Passive attack: unauthorized reading of data.
Attempts to learn or make use of information from the system
Does not affect system resources.
Hard to detect
Encryption prevents the success of passive attacks.
Goal: obtain information that is being transmitted.
Types
I) Release of message content
II) Traffic Analysis (location, identity, length of message, frequency, etc.), i.e., observe the pattern of the message.
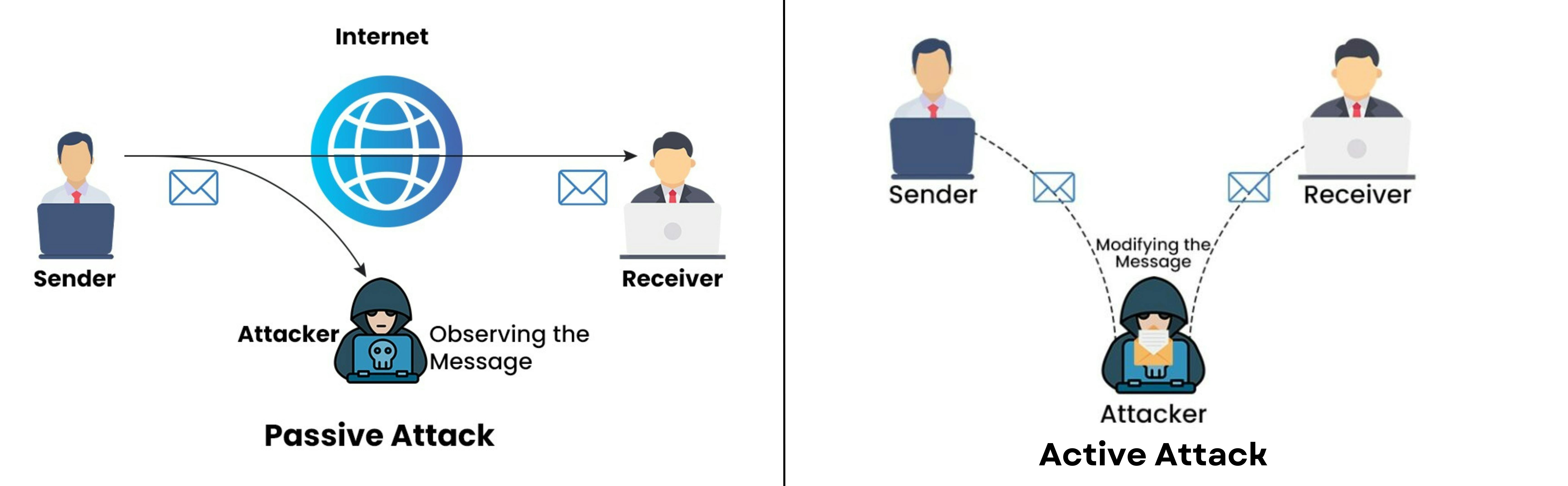
Active attack: involves some modification of the data stream or the creation of a false stream.
difficult to prevent
immediately act upon it once detected.
Types
I) Masquerade (Mask to act as someone else)
II) Replay (more than one message will be sent)
III) Modification of message
IV) DOS (Denial of Services)
🛠️Security Services
Security services are processing or communication services that are provided by a system to give a specific kind of protection to system resources. Security services implement security policies and are implemented by security mechanisms.
Authentication: assures the authentic identity of the sender
Peer entity authentication
Data origin authentication
Access control: levels of controls provided, i.e., grant or revoke access
Data confidentiality: Remains Confidential
Data Integrity: Originality maintains
Non-repudiation: proof of data being sent on both sides, viz., sender and receiver.
🦾Security Mechanisms
Specific security mechanisms
I) Encipherment
II) Digital Signature
III) Access Control
IV) Data Integrity
V) Authentication Exchange
VI) Traffic Padding
VII) Routing Control
VIII) Notarization
Pervasive security mechanisms
I) Trusted Functionality
II) Security Label
III) Event detection
IV) Security Audit trail
V) Security recovery
🔏Cryptography
The art of science encompasses the principles and methods of transforming an intelligible message into one that is unintelligible and then retransforming that message back to its original form.
✌️Types of cryptography
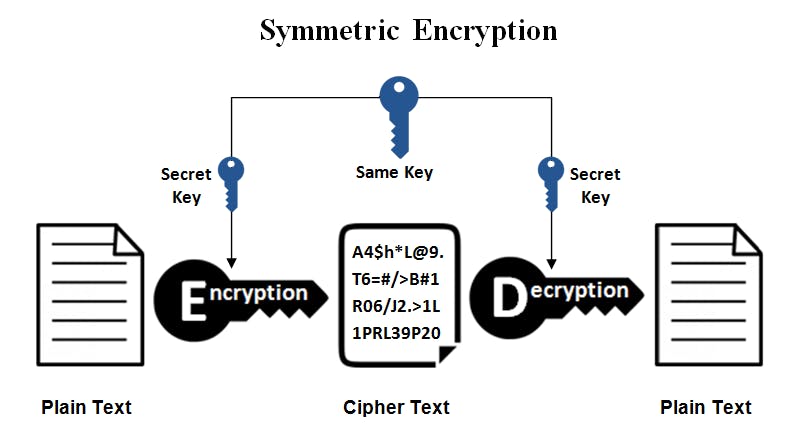
Symmetric Cryptography (Private): The simplest kind of encryption that involves only one secret key to cipher and decipher information.
It uses a secret key that can either be a number, a word, or a string of random letters.
The sender and the recipient should know the secret key that is used to encrypt and decrypt all the messages.
Blowfish, AES, RC4, DES, RC5, and RC6 are examples of symmetric encryption. We will see these algorithms in future blogs.
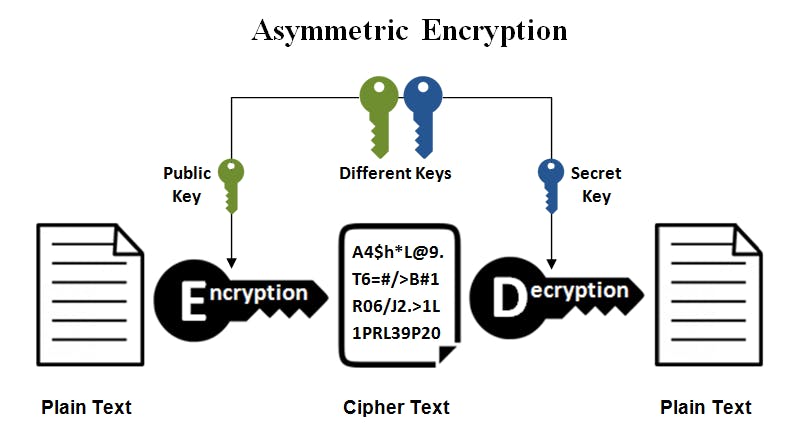
Asymmetric cryptography (public): Asymmetric encryption uses two keys to encrypt plain text. Secret keys are exchanged over the Internet or a large network.
It ensures that malicious people do not misuse the keys. It is important to note that anyone with a secret key can decrypt the message, and this is why asymmetric encryption uses two related keys to boost security.
A public key is made freely available to anyone who might want to send you a message. The second private key is kept secret so that you can only know it.
Popular asymmetric key encryption algorithms include EIGamal, RSA, DSA, and elliptic curve techniques.
𓀝Cryptanalysis
Cryptanalysis is the process of analyzing and breaking cryptographic systems, including ciphers, cryptosystems, and encrypted text, without possessing the secret key.
Deciphering ciphertext without knowledge of the plaintext source, encryption key, or decryption algorithm

Passive attacks involve eavesdropping on or monitoring communications without modifying or altering the data. The attacker does not interact with the encryption system, but rather observes the encrypted messages and tries to decipher them. Some examples of passive attacks include:
Ciphertext-only attack (COA): The attacker only has access to encrypted messages (ciphertext) and tries to decipher them without any knowledge of the plaintext or the encryption key.
Known-plaintext attack (KPA): The attacker has access to some pairs of plaintext and ciphertext and tries to use this information to decipher other encrypted messages.
Chosen-plaintext attack (CPA): The attacker can choose any plaintext messages they want and then observe the corresponding ciphertext. This type of attack is more powerful than KPA, as it allows the attacker to carefully select plaintexts that are likely to reveal information about the encryption algorithm or key.
Active attacks involve modifying or altering the data being transmitted. The attacker interacts with the encryption system in an attempt to manipulate the data or the encryption process. Some examples of active attacks include:
Man-in-the-middle attack (MITM): The attacker intercepts communications between two parties and inserts themselves into the conversation. This allows them to eavesdrop on the communications, modify the data, or even impersonate one of the parties.
Replay attack: The attacker intercepts an encrypted message and stores it. They can then replay the message later to gain access to the plaintext.
Substitution attack: The attacker replaces an encrypted message with a different encrypted message. This can be used to manipulate the data or redirect the communication to a different destination.
Substitution techniques are a type of cryptographic method that replaces characters in plaintext with other characters, numbers, or symbols according to a predetermined rule. This technique is used to make the plaintext unreadable to anyone who does not have the secret key.
🔀Substitution technique
There are two main types of substitution techniques: monoalphabetic and polyalphabetic.
Monoalphabetic substitution
In monoalphabetic substitution, each character in the plaintext is always replaced with the same character in the ciphertext. This type of substitution is relatively easy to break, as frequency analysis can be used to identify the most common characters in the ciphertext and deduce the corresponding plaintext characters.
Example:
Plain text: "Hello, world!"
Ciphertext: "Ufntf, xjuf!"
In this example, each letter of the alphabet is replaced with the letter three positions down the alphabet (A becomes D, B becomes E, etc.).
Polyalphabetic substitution
In polyalphabetic substitution, each character in the plaintext is replaced with a different character in the ciphertext, depending on its position in the text. This type of substitution is more difficult to break than monoalphabetic substitution, as the frequency analysis cannot be used as effectively.
There are many different types of polyalphabetic ciphers, but some of the most common include:
Vernam cipher: The Vernam cipher works by XORing each plaintext character with the corresponding character in a random key. This means that each plaintext character can be replaced with any one of 256 different ciphertext characters, depending on the key.
Steps of the Vernam cipher:
Assign the number to each character of plain text and the key according to the alphabetical order.
Perform bitwise xOR operations on both numbers, where one is the corresponding plain text character number and the other is the key character number.
Subtract the number from 26 if the resulting number is greater than or equal to 26, and if it is not, then leave it.
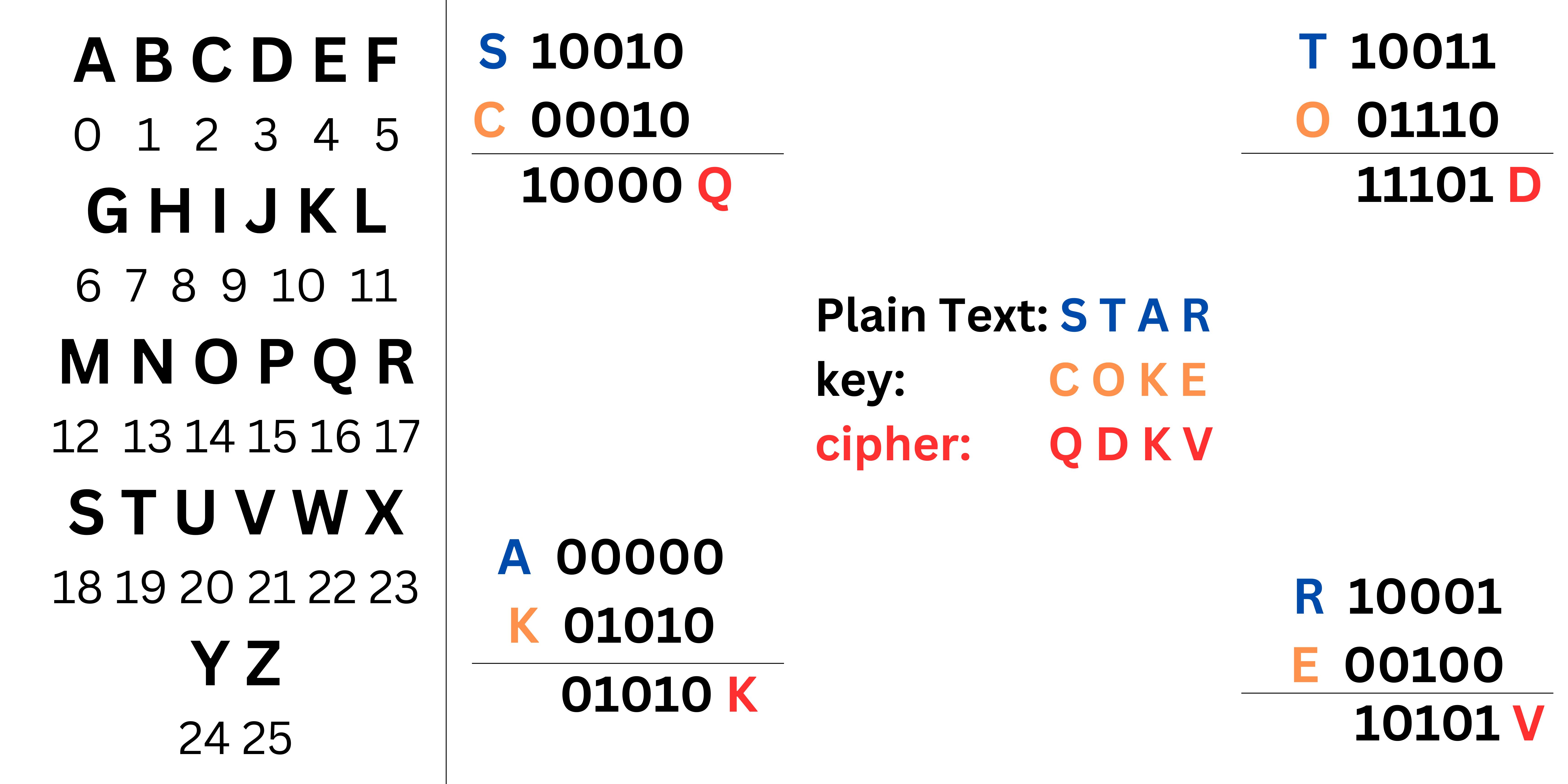
Caesar cipher: This is a type of monoalphabetic substitution cipher in which each letter of the alphabet is shifted by a fixed number of positions. For example, in a Caesar cipher with a shift of 3, A becomes D, B becomes E, and so on.

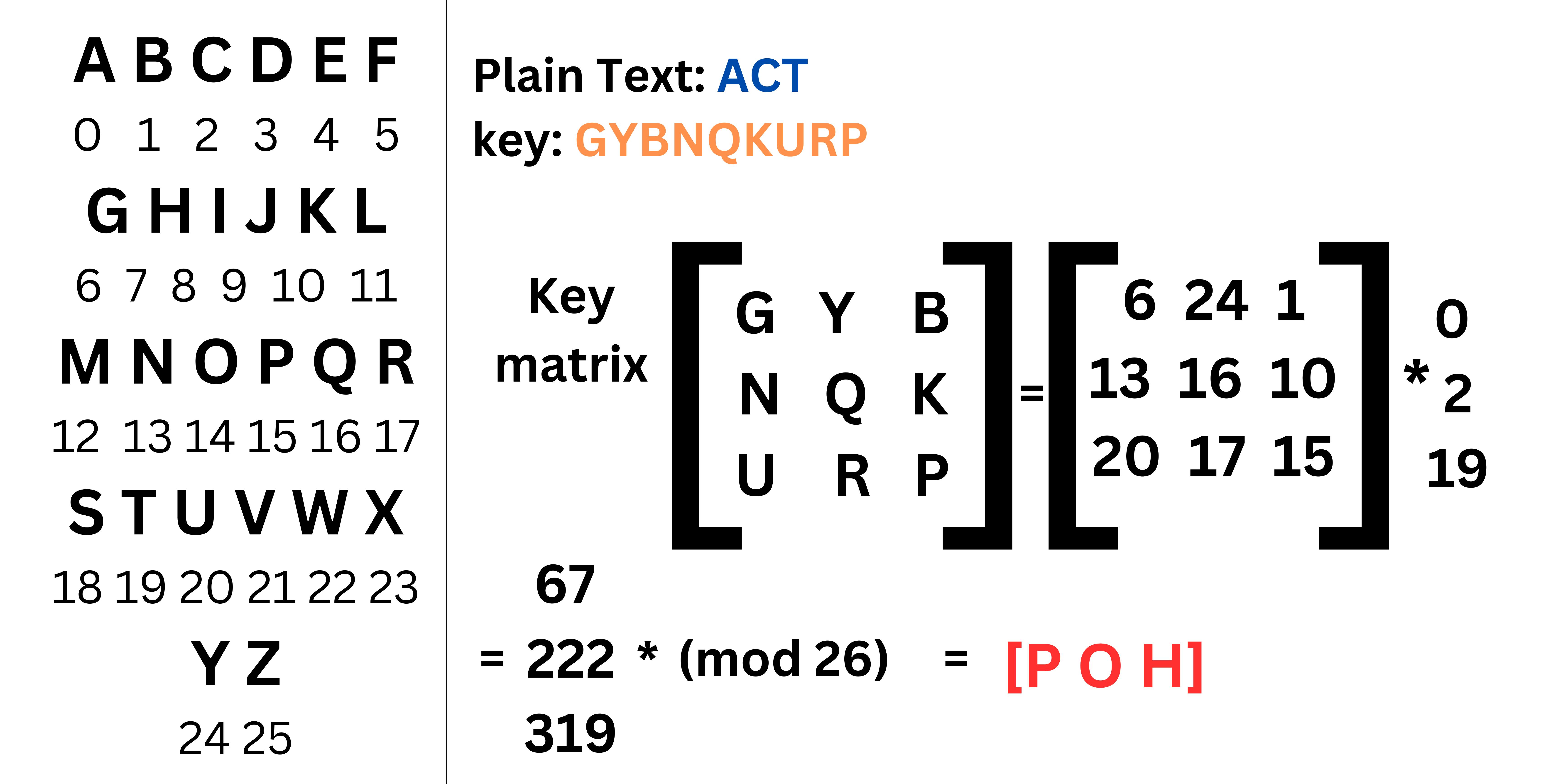
Hill Cipher: The Hill cipher, on the other hand, is a type of affine cipher. In an affine cipher, each plaintext character is multiplied by a constant and then added to another constant. This means that each plaintext character can only be replaced with a single ciphertext character.
Steps of the Hill Cipher:
Choose a key matrix The key matrix must be invertible, which means that it must have a determinant that is not zero. The size of the key matrix determines the block size of the cipher, which is the number of letters that will be encrypted at a time. For example, a 2x2 key matrix will encrypt two letters at a time, while a 3x3 key matrix will encrypt three letters at a time.
Pad the plaintext. If the plaintext message is not a multiple of the block size, it must be padded with extra characters. This can be done by adding one or more spaces to the end of the message.
Divide the plain text into blocks. Divide the plaintext message into blocks of size equal to the block size of the cipher.
Convert each block of plaintext into a vector. Each block of plaintext is converted into a vector by assigning a numerical value to each letter. For example, A could be represented as 0, B could be represented as 1, and so on.
Multiply each block vector by the key matrix.
Convert each ciphertext vector back into a block of ciphertext. Each ciphertext vector is converted back into a block of ciphertext by converting each numerical value back into a letter.
Concatenate the ciphertext blocks. The ciphertext blocks are concatenated to form the final ciphertext message.
Playfair cipher: This is a type of polyalphabetic substitution cipher that uses a 5x5 grid of letters. Each pair of adjacent letters in the plaintext is replaced with a pair of letters from the grid, according to a specific rule.
Steps of the Playfair cipher:
Choose a keyword. The keyword is used to generate the key table. The keyword should be a memorable phrase or word that is not too short or too long.
Create the key table. The key table is a 5x5 matrix that is filled in with the letters of the alphabet, excluding any repeated letters. The order of the letters in the key table is determined by the keyword.
Divide the plaintext into digraphs. The plaintext message is divided into pairs of letters called digraphs. If there is an odd number of letters, the last letter is doubled.
Apply the encryption rules. There are two rules for encrypting digraphs:
If both letters are in the same row, replace each letter with the letter to its right in the row. If there is no letter to the right, wrap around to the beginning of the row.
If both letters are in the same column, replace each letter with the letter below it in the column. If there is no letter below, wrap it around to the top of the column.
If the two letters do not share a row or column, draw a rectangle with the two letters as opposite corners. Replace each letter with the letter at the opposite corner of the rectangle.
Concatenate the encrypted digraphs. The encrypted digraphs are concatenated to form the ciphertext message.
Here is an example of how to encrypt the message "ATTACK" using the Playfair cipher with the keyword "MONARCHY":
Key Table: M O N A R C H Y B D E F G I J K L P Q S T U V W X Plaintext: AT TA CK Encrypted: FX OX NP
Vigenère cipher: This is a type of polyalphabetic substitution cipher that uses a keyword to determine the substitution rule. The keyword is repeated over and over again, and each letter of the plain text is replaced with the letter of the keyword that corresponds to its position in the text.
Steps of the Vigenere cipher:
Choose a keyword: Select a memorable keyword or phrase that will serve as the basis for the encryption shifts.
Prepare the Plaintext: Ensure the plaintext is in uppercase and remove any non-alphabetical characters.
Create a Vigenère Square: Construct a 26x26 table with the alphabet written repeatedly in each row, starting with a different letter in each row. This table will be used for the encryption shifts.
Repeat the Keyword: Repeat the keyword to match the length of the plaintext. This will provide a shift value for each plaintext letter.
Apply Vigenère Shifts: For each plaintext letter, locate its corresponding row in the Vigenère Square using the keyword letter as the row header. Then, locate the column index corresponding to the plaintext letter. The letter at the intersection of this row and column is the ciphertext letter.
Concatenate Ciphertext Letters: Combine the encrypted letters to form the ciphertext message.
Example:
Plaintext: "ATTACK AT DAWN"
Keyword: "LEMON"
Ciphertext: "KXFMGC UFCHFL"

Java code for the Vigenere cipher
Substitution techniques are a fundamental part of cryptography, and they have been used for centuries to protect sensitive information. While modern cryptographic algorithms are much more complex and secure than the substitution ciphers of the past, the basic principles of substitution remain the same.
↗️↘️Transposition Cipher
In cryptography, a transposition cipher is a method of encryption that rearranges the letters of the plaintext (the original message) to create the ciphertext (the encrypted message). Transposition ciphers do not change the letters themselves, but simply the order in which they appear. This makes them more difficult to break than substitution ciphers, which replace letters with other letters.
There are many different types of transposition ciphers, but some of the most common include:
Rail fence transposition: In rail fence transposition, the plaintext is written out in a zigzag pattern and then read out horizontally.
Plain text: MASTER
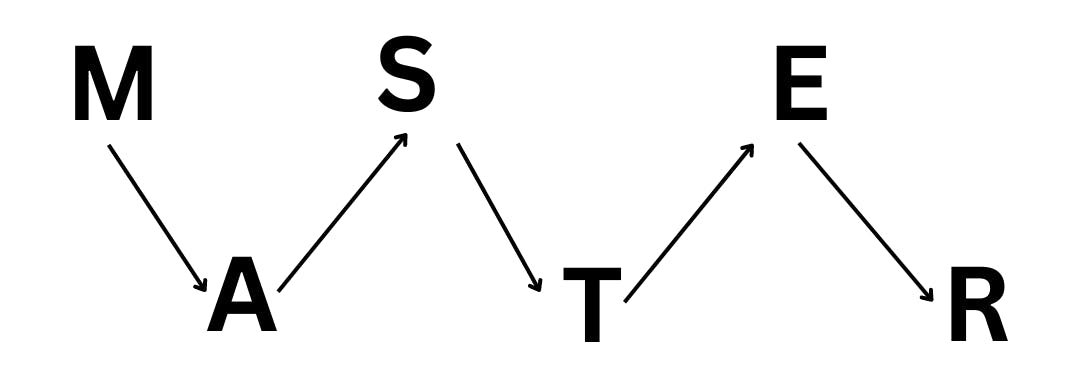
ciphertext: MSEATR
Java code for the Rail Fence cipherAlthough this marks the end of Unit 1, it's not the conclusion of our exploration into cryptography and network security. Stay tuned for the next chapter. Until then, keep learning and growing!